And forget not that the earth delights to feel your bare feet and the winds long to play with your hair.
– Khalil Gibran
To be a pilot of a small plane is to be a scientist, a mathematician, and a poet. We read charts, analyze weather reports and forecasts, calculating what the headwinds will do to our fuel situation.
But in the end, the wise ones let the earth speak to us through these charts, and go where it invites us — where the skies are smooth and blue.
And so it was last week that we did not go to California as planned, but instead to the mountains near Santa Fe, a canyon near Amarillo, and a remote museum in far southwest Kansas — all the while hearing the delighted exclamations of “wow!” from our children.

As we sailed along up there in our flying machine, down below we saw the rugged, craggy mesas of New Mexico, here and there punctuated by a lake, a little town, or an isolated airport — each a friendly sight in its own way. Our boys read some books, and sometimes pressed their noses to the windows, while little Martha mostly slept and sometimes played or ate — she enjoys flying more than driving.

Mountains have a way of reminding us all that the earth is larger than we are. We drive around them, fly around them, and even on a pleasant day they make the air bumpy. But once down on the ground, Oliver got out of the plane, and looked at the mountains all around us. He couldn’t stop saying “Wow! Dad, wow! Amazing! Look at that!” Jacob was more excited that an American Airlines plane was taxiing by right where we had been a minute before.

The boys helped us plan our trip. They’re the ones that chose for us to head southwest, and the #1 thing on their Santa Fe agenda was riding the New Mexico Rail Runner Express. So, despite a strong and cold wind, ride it we did, all the way to Albuquerque for pizza, then back to Santa Fe. When they weren’t busy listening to the “meep meep” sound the doors make when they’re about to close, they were excitedly reading the timetable or taking in the world as it whizzed past their window.

Martha, too, took in the train — though she still enjoyed her chew toys. Those things out the window don’t fit into a mouth so easily.

Up in the mountains, the Puye Cliff Dwellings brought home the history of the place. The stories of the peaceful people that lived there, told by their descendants, members of the Santa Clara pueblo. Our guide Elijah picked up a shard of pottery, many of which remain on the mesa. He explained why there were no intact pottery examples up there. When his ancestors were done with a pot, then would throw it on the ground, shattering it — to give it back with thanks to the earth from where it came. One gets the sense that these ancient peoples knew quite a few things that our modern societies have not yet learned.

After a full day, a cool evening in our hotel was welcome. Our room had a wood-burning fireplace, burning the pinyon pine that gives Santa Fe such a distinct sweet smell in the winter. Jacob would gaze into the fireplace for quite awhile.

I have never seen a photo do justice to Palo Duro Canyon. As you drive along the desolate, high Texas prairie, complete with tumbleweeds, all of a sudden you go around a corner and the earth opens up. It’s the “painted canyon” for a reason, and even though we’d been there before, as we rounded that bend, I heard exclamations of “Dad, this is AMAZING” from the back seat once again.
The vastness of the place cannot be captured on a screen. How can one capture 60 miles of color, ridges and gorges stretching out into the horizon, in a few inches?

The boys were excited, bubbly, and bouncy as we hiked along some trails on the canyon floor. They’d make up games to play, most of which involved teasing me in some way.

Oliver particularly loved to tease me.

Jacob insisted I take a picture with him and Martha.

But even these excited, bubbly kids would stop to reflect sometimes. Sometimes Jacob would say, “Dad, I have GOT to take a picture of this!” And sometimes they would just stare, maybe even with a mouth agape. Children know beauty, too.

The three siblings delight in each other, too. Oliver would play a version of peek-a-boo, saying “I’m alive! Horse pill!” (he’d say silly things, and whatever made Martha laugh he’d keep saying.)
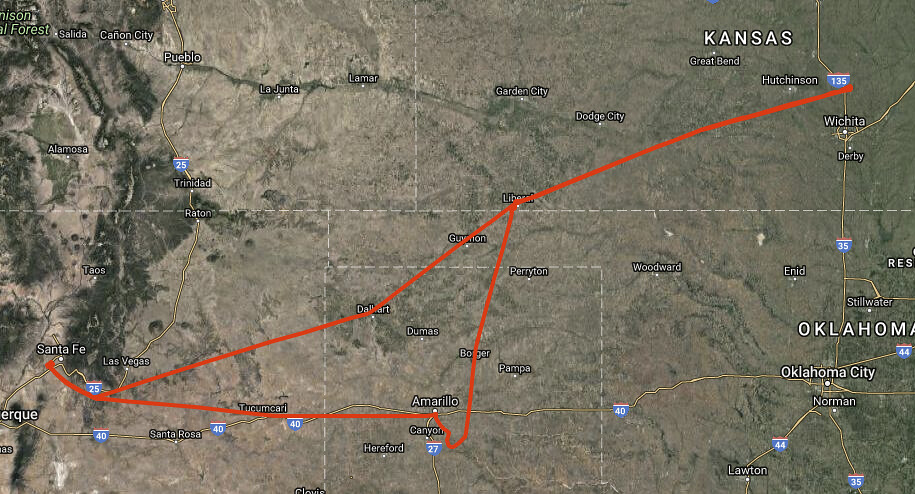
All told, we traveled over a thousand miles by air, spending some 7 or 8 hours in the plane. Had we attempted to drive it, it would have been more than 30 hours. There’s something amazing about seeing so much of the world in such a short amount of time.

Perhaps this is why many pilots secretly give their plane a little pat after a long journey. After all the smiles, laughter, the memories, the feeling of being part of sky — if you pay attention, it truly is more poetry than physics.
And that is why, though it is always nice to return to our home, in my mind’s eye, the hangar door is always open.